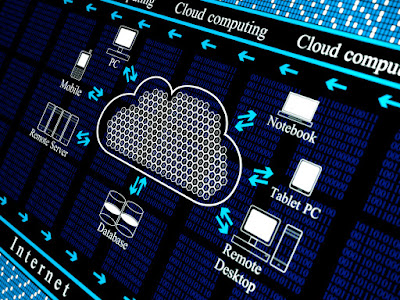
Cloud computing is currently an integral part of operations for many companies. Information management becomes more efficient with the storing, managing, and processing of data on a network of remote servers hosted on the internet. And it is just one of the array of benefits any company will get from cloud computing.
Image source: cloudcomputing-news.net
Storage management
Cloud computing can assist with management of data. There are three types of services to choose from: public, private or hybrid. All kinds come with built-in data reduction that can improve data protection.
Data encryption
Hackers are always on the prowl for files and information that they can access remotely through malicious software. Companies that enlist cloud computing services can be assured of data encryption and protection against hacks.
Image source: defensedaily.com
Disaster recovery
The feature most companies look for in cloud computing services is disaster recovery. This ensures companies that their files can be restored immediately after a system breakdown.
As companies take advantage of the benefits cloud computing, they can be assured of business continuity as their IT system becomes safer and more reliable.
CITOC provides businesses in Texas expert IT solutions, including planning and security services. Visit its official website for more information.